Hey, guys! How y’all doing?
Today, we’re going to take a look at an arrest that happened in Morocco as the result of a joint- 2-year investigation by the INTERPOL, the Morrocan police and security firm Group-IB. A highly sought-after cybercriminal, who calls themselves ‘Dr HeX’ and has lived off phishing scams for the past 9 years, has finally been apprehended!
Ain’t that some good news?
Who is ‘Dr HeX’?
Nicknamed ‘Dr HeX’, this threat actor is responsible for scamming victims via phishing, website defacing malware development, fraud and carding - for a solid 9 years.
In May 2021, INTERPOL arrested a Moroccan man who is suspected of being the famous ‘Dr HeX’. During this 2-year probe dubbed ‘Operation Lyrebird’, the Morrocan police and Group-IB were working closely with INTERPOL to make the bust.
Upon further investigation, it was understood that the unnamed suspect was involved in the development of carding and phishing kits to be sold in illegal online forums. An example of a carding site would be Joker’s Stash. Taken down back in December 2020, Joker Stash was a destination criminals favoured when it came down to trading payment-card data and buying stolen credit and debit cards.
Besides that, according to Group-IB’s research, the Morrocan man was apparently involved in attacks on 134 websites from 2009 to 2018, in which he had left his signature ‘Dr HeX’ nickname on the compromised web pages. However, it seems the mystery Morrocan man has multiple nicknames though, ‘Dr HeX’ is the nickname Group-IB chose to dub the threat actor whom they tracked.
What can one do with ‘Dr HeX’s’ carding and phishing kits?
Buyers of the kits can masquerade as online-banking facilities, which allows them “to steal sensitive information and defraud trusting individuals for financial gain, with the losses of individuals and companies published online in order to advertise these malicious services”, according to INTERPOL’s announcement.
A sample use case of how the carding economy works is the Dallas-based smoked-meat franchise Dickey’s Barbeque Pit incident back in October 2020. In this incident, 3 million customer payment cards were exposed. Anyone who gets their hands on this data can simply create cloned cards. These cloned cards can be used physically at ATMs or at in-store machines that aren’t chip-enabled. Another possibility is to use the exposed payment-card data for online purchasing.
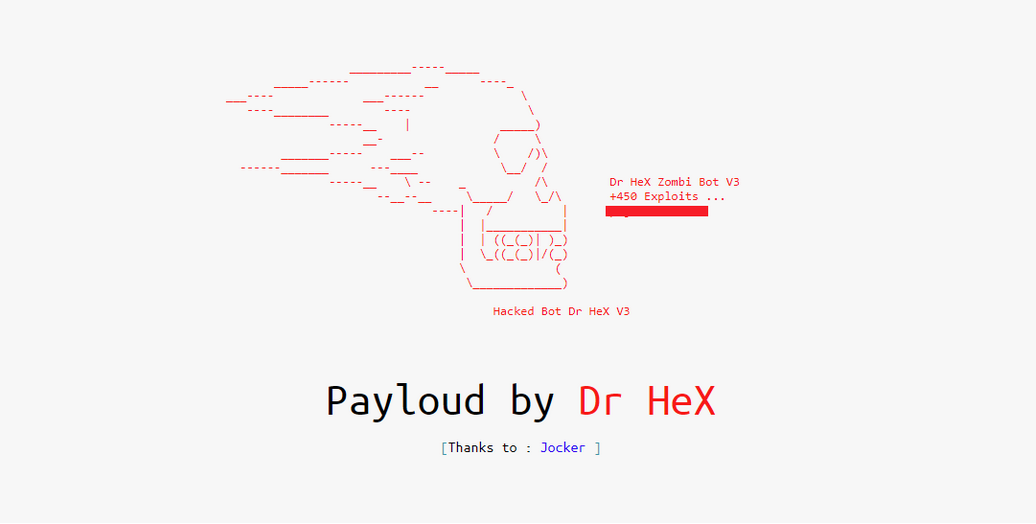
Figure 1: One of Dr HeX’s carding and phishing kits
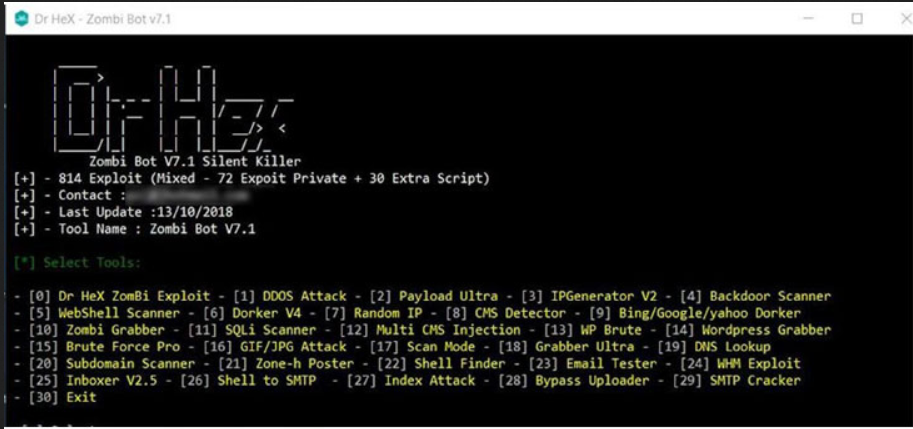
Figure 2: Another kit by Dr HeX called ‘Zombi Bot’
Group-IB CTO, Dmitry Volkov, says this about Zombi Bot:
“The suspect, in particular, promoted the so-called Zombi Bot, which allegedly contained 814 exploits, including 72 private ones, a brute-forcer, webshell and backdoor scanners, as well as functionality to carry out DDoS attacks.”
What’s the starting point behind unmasking ‘Dr HeX’?
The starting point was the extraction of a phishing kit - a tool used to create phishing web pages. According to Group-IB, this phishing kit was used to exploit the brand of a large French bank.
According to Group-IB,
“The phishing kit used a typical setup, which included the creation of a spoofed website of a targeted company, the mass distribution of emails impersonating it and asking users to enter login information on the spoofed site. The credentials left by unsuspecting victims on the fake page were then redirected to the perpetrator’s email.”
Apparently, almost all of the scripts contained in the phishing kit were signed with the signature of their creator, ‘Dr HeX’, and had a contact email address. The threat actor must’ve adored that nickname in particular, especially because Group-IB researchers found that the alleged attacker’s YouTube channel was signed under that same name. Bingo!
Besides that, in one of the videos of the unnamed suspect’s YouTube channel, he had left a link that led to an Arabic crowdfunding platform. This became another useful linkage to Group-IB researchers to the alleged cybercriminal.
Group-IB said:
“The name was also used to register “at least” two domains that were created with the email found in the phishing kit.”
Based on the email ID from the phishing kit, other components of the threat actor’s malicious infrastructure started to unfold.
- 5 email addresses
- 6 nicknames
- Accounts on Facebook, Instagram, Skype and YouTube.
During the 9 years (from 2009 to 2018), ‘Dr HeX’ has defaced 134 web pages as mentioned earlier. Apparently, there were some posts discovered by the security firm.
According to Group-IB,
“The posts revolve around several popular underground platforms intended for malware trading that indicate the latter’s involvement in malware development.”
Besides that, analysts also found evidence that might link ‘Dr HeX’ to attacks on several huge French corporations with the aim of stealing customer’s bank-card data.
Stephen Kavanagh, INTERPOL Executive Director of Police Services says:
“Operation Lyrebird is a significant success against a suspect who is accused of targeting unsuspecting individuals and companies across multiple regions for years… The case highlights the threat posed by cybercrime worldwide… The arrest of this suspect is down to outstanding international investigative work and new ways of collaboration, both with Moroccan police and our vital private sector partners such as Group-IB.”
So, there you have it! For more interesting news and updates, sit tight and stay tuned.
Until next time, friends!
Credits: Threatpost, TheRecord, The Hacker News