Hey, guys! How are y'all doing today?
Today, we’re going to look into the new tactic of infection of the LockBit 2.0 ransomware: socially engineering targets via fake copyright infringement emails. Though LockBit isn’t the first or the only malware that has chosen phishing emails for malware distribution, the story they chose to convince targets and the way they have gone about the whole operation is quite interesting.
Curious, yet? Let’s understand the whole story, shall we?
The Story
Unsuspecting users receive emails about copyright violations that they have apparently committed by allegedly using media files without the creator’s license. These emails end in a not-so-friendly note where they demand the removal of the infringing content from the recipient’s website, or risk facing legal action.
The catch is, the emails don’t specify which files were unethically used in the recipient’s website. Instead, the emails instruct recipients to download and open the attached file to view the infringed content. Obviously, the attachment is where the ransomware resides - waiting to be triggered.
These emails were first spotted by analysts in AhnLab in South Korea.
The Attachment
The amount of thought process gone into the creation of the attachment in such a way that it evades detection by email security tools depicts the dedication of LockBit 2.0 ransomware operators.
The attachment was a password-protected ZIP archive consisting of a compressed file. This compressed file happened to be an executable disguised as a PDF document. In the end, it is an NSIS installer.
The victim sees a compressed ZIP file, which upon file extraction, becomes a PDF document. The moment they open the PDF document, the ransomware loads and encrypts the device with the LockBit 2.0 ransomware.
As mentioned, LockBit ransomware gang isn’t the only one conning people with the copyright violation claim. In other emails with the same story, the distribution of BazarLoader and Bumblebee malware loader were discovered.
LockBit 2.0 ransomware attacks
According to NCC Group's "Threat Pulse" report for May 2022, 40% of all (236) ransomware attacks were caused by LockBit 2.0.
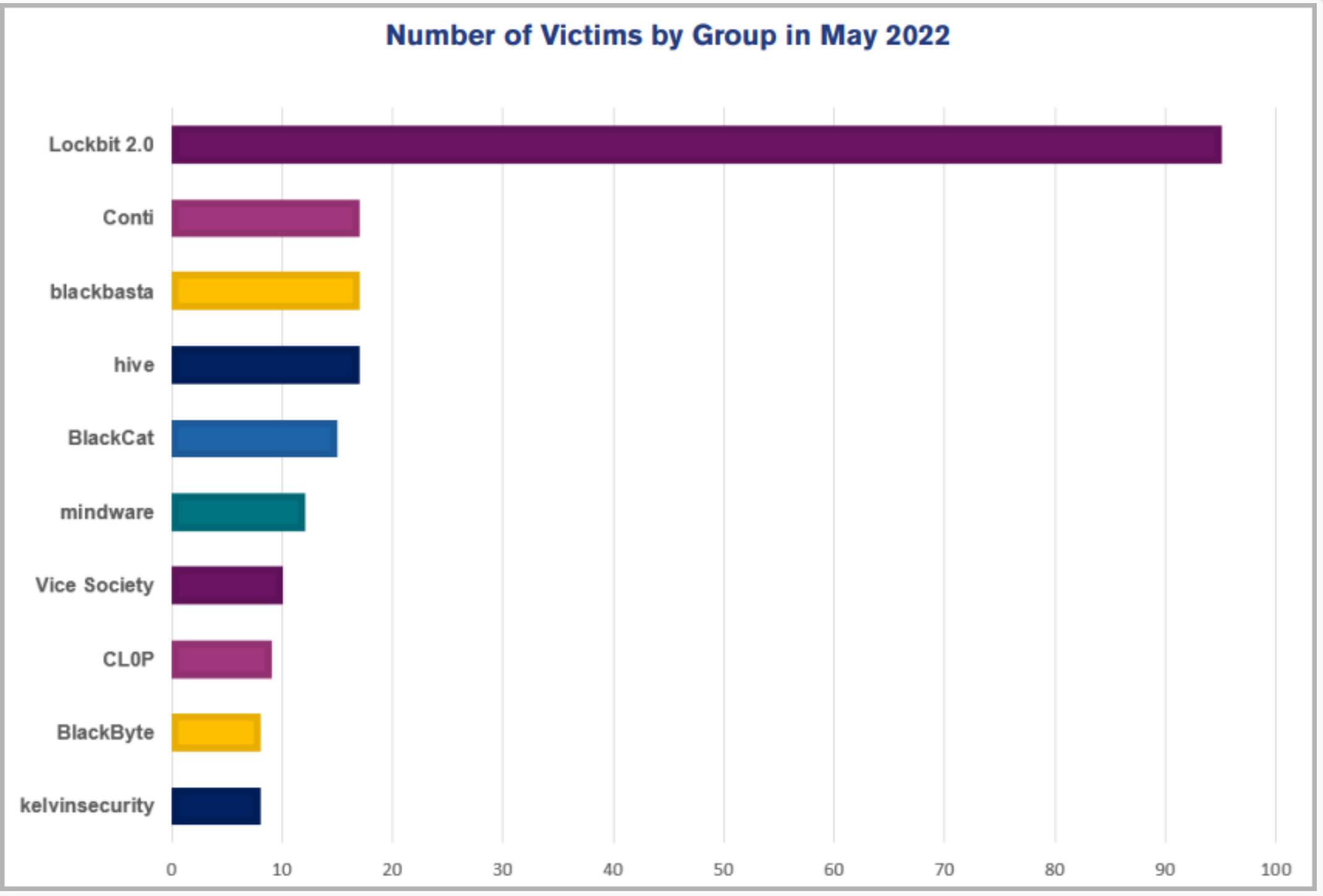
Figure 1: Ransomware operation in May 2022
LockBit 2.0 had 95 victims in May alone while other ransomware were dabbling with less than 20 victims each.
To add on, LockBit 2.0 operators have made it very clear that they are not in any way affiliated with Russia-based cyber gangs and even went the extra mile to prove their point - via a publicity stunt.
The success of LockBit 2.0 will likely continue as it has recently officially released the third generation of ransomware strains. According to a security research group VX-Underground, LockBit even offers a bug bounty program, often associated with large software companies.
So, there you have it! For more interesting news and updates, sit tight and stay tuned.
Until next time, friends!
Credits: BleepingComputer, Cybernews