Hey, guys! How y’all doing?
Today, we’re going to take a look at a malware whose operators thought it needed some improvement to better evade detection mechanisms and slow down investigative analysis in order to continue victimising unsuspecting targets.
Debuted back in 2019, Buer malware, which is often used to deliver second-stage payloads, is predominantly used by cyber criminals to gain initial access on networks. This access is either exploited by the attackers themselves or sold to other attackers to perform their own malware campaigns - most commonly, ransomware attacks. The trojan downloader is sold to cybercriminals through a “malware-as-a-service” payment model.
Now that we got to know Buer on the surface level, let’s get more acquainted!
How was Buer revamped?
The malware has been completely rewritten in a new language!
Previously written in C programming language, Buer has now been discovered to be rewritten in a different, lesser-known language - Rust programming language. While it’s usual to come across malware written in C, C+, Python and Java, threat actors have also been known to play around with more obscure languages as a way to stay ahead of detection and forensics.
According to Sherrod DeGrippo, Senior Director of Threat Resarch and Detection at Proofpoint, RustyBuer presents challenges or signature-based detections that are based on how the malware behaves when executed in a sandbox environment.
“Malware written in C and malware written in Rust will behave differently in a sandbox environment. For example, RustyBuer uses its own TLS library. While the malware executed as expected, we had to make a few adjustments so that we could see all of the C2 communications.”
This new variant, uncovered by cybersecurity researchers at Proofpoint, is effective in aiding attackers’ latest campaigns to be under the radar in attacks against Windows systems. They’ve named this variant ‘RustyBuer’.
Proofpoint says:
“Rewriting the malware in Rust enables the threat actor to better evade existing Buer detection capabilities.”
How is this malware now being used?
RustyBuer is propagated via phishing emails that are designed to present themselves as legitimate emails from renowned delivery company, DHL. These malicious emails ask users to download a Microsoft Word or Excel document that supposedly details information about a scheduled delivery. The document apparently contains “international information” regarding a shipping order and asks victims to download a file, named “Private File.”More than 200 organizations across more than 50 verticals have been sent such fake emails.
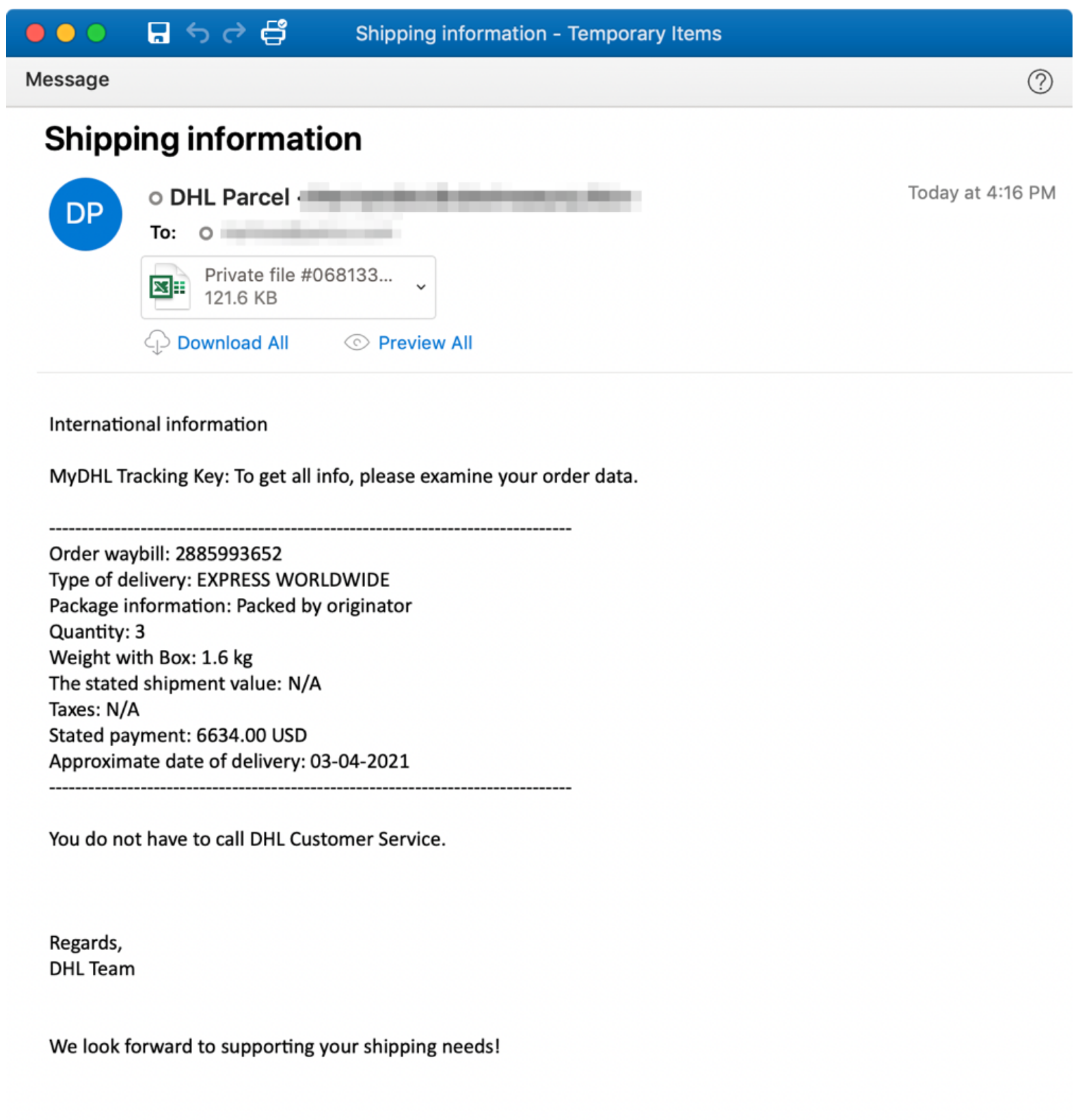
Figure 1: Fake email from ‘DHL’
Obviously, the ‘scheduled delivery’ is fake but victims still fall for it since online purchasing has drastically increased due to the COVID-19 pandemic. As such, emails or messages claiming to come from delivery services have become an effective way to trick people into opening phishing emails and downloading malicious files.
In this particular case, the infected document asks users to enable ‘editing mode’ which enables macros that give way for malware execution. The bogus document claims that enabling ‘editing mode’ is required because the document is ‘protected’. To appear legitimate, the document even uses a few anti-virus providers’ logos to fool users.
Figure 2: Anti-virus brand logos used to make the fake document appear more genuine
Once macros are enabled, the RustyBuer malware is dropped into the victim machine. This essentially provides attackers with a backdoor to enter in and out of the network as well as further inflicting the victim with other attacks - which includes ransomware. According to researchers, the macros leverage an Application Bypass (Windows Shell DLL via LOLBAS) to evade detection from endpoint security mechanisms.
Experts say it’s unusual for malware to be given a new look this way but it goes to show just how much effort the Buer operators are putting into making their product a success. The new version of Buer is being sold in the dark web forums where potential buyers have the option of either freshly compromising a victim from scratch using the malware or gaining access to an already-infected system - aka access-as-a-service model.
Proofpoint researchers say:
“The rewritten malware, and the use of newer lures attempting to appear more legitimate, suggest threat actors leveraging RustyBuer are evolving techniques in multiple ways to both evade detection and attempt to increase successful click rates … Based on the frequency of RustyBuer campaigns observed by Proofpoint, researchers anticipate we will continue to see the new variant in the future.”
Jerome Segura, Director of Threat Intelligence at MalwareBytes says:
“During the past few years we have noticed that malware authors are adopting newer coding languages at a more rapid pace … The first one that quickly gained popularity was Golang or Go, used by many different threat actors and for a wide array of malware families, including ransomware. As a developer, Go provides a number of advantages such as cross-platform compilation – write once, deploy on multiple OSes – and is also not as well known among reverse engineers … A full rewrite of Buer Loader in the Rust language is no small amount of work. By choosing Rust, the malware authors are giving criminals who use this Buer loader variant an increased chance at flying under the radar and deploying the payload of their choice. That, in itself, can be one of the key differentiators with other competing loaders on the market.”
Threat Analyst, Nikko Tamana, from Tren Micro has a technical take on this malware.
“The degree of difficulty would be influenced by how ‘detached’ the programming language is to the most popularly used ones … The attackers also don’t lose any key functionalities by switching to Rust. For instance, like Golang and C, Rust supports multiple OS platforms and thus targets not just Windows, but Linux … And Rust features secure memory management, which ‘creates a lower chance that the exploit will fail due to memory mismanagement without the trade-off of performance. Other programming languages use a garbage collector to clean unused memory spaces automatically, but that trades off some performance’ … Since Rust has secure memory management, is cross-platform, and is usually used for system programming – meaning it allows computer hardware to interface with programmer and user – it might be a good programming language for small systems or systems with hardware limitations such as IoT.”
The Buer loader has previously been spotted as recently as February, when researchers with Infoblox uncovered a Buer campaign using invoice-themed lures to persuade victims to download and open Microsoft Excel (XLS) documents, which contained malicious macros and distributed the malware.
How to protect against this malware?
Most malware and their variants - including Buer and RustyBuer - can be prevented from running from successful phishing emails by simply disabling macros in Microsoft Office products. So, if you don’t need macros, disable them!
So, there you have it! For more interesting news and updates, sit tight and stay tuned.
Until next time, friends!
Credits: ZDNet, SC Magazine, Decipher,