Hey, guys! How are y’all doing today?
Recently, security researchers from Singapore University of Technology and Design revealed a rather unsettling discovery regarding the Bluetooth technology. They have found a family of 20 security flaws, which they collectively call ‘BrakTooth’.
The main reason BrakTooth is the talk of the town today is due to the fact that it affects more than 1,400 products based on 13 different Bluetooth devices sold by 11 of the world's leading vendors. The impact is huge!
Let’s understand BrakTooth better to know the full extent of the impact.

What kind of devices can fall victim to BrakTooth?
For their initial tests, the researchers only examined the Bluetooth software libraries for 13 System-on-Chip (SoC) boards from 11 vendors.
However, subsequent research found that the same Bluetooth firmware was most likely used inside more than 1,400 chipsets, used as the base for a wide assortment of devices.
These devices could be:
- smartphones,
- laptops,
- keyboards,
- headphones,
- Industrial equipment,
- other Bluetooth-enabled devices.
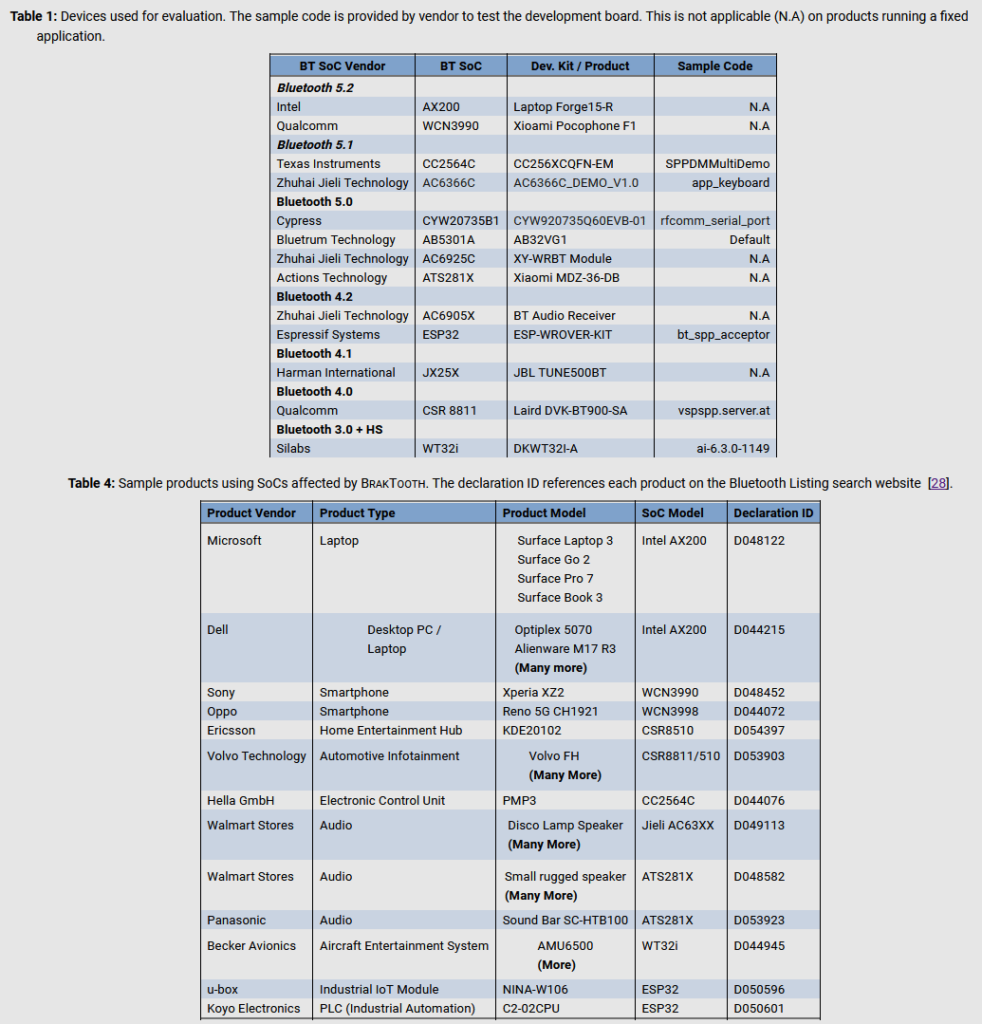
Figure 1: Summary of devices used for evaluation and list of devices affected by Braktooth
The bad news doesn’t stop there. 1, 400 is just the minimum number of devices that can be affected by BrakTooth!
According to the researchers:
"As the BT stack is often shared across many products, it is highly probable that many other products (beyond the ≈1400 entries observed in Bluetooth listing) are affected by BrakTooth."
What is BrakTooth capable of?
BrakTooth can reportedly be exploited to conduct Denial-of-Service (DoS) attacks and enable arbitrary code execution on target devices.
The DoS attacks can disrupt the victim's Bluetooth connection or, in some cases, require Bluetooth connectivity to be restarted manually while arbitrary code execution can be used to erase user data, disable wireless connectivity, or interact with other devices.
The only good news is that BrakTooth only allows for arbitrary code execution on the ESP32 system on chip (SoC) made by Espressif Systems. However, ESP32 is commonly found in Internet of Things (IoT) devices as well as industrial systems. This SoC is so common that the researchers' proof of concept exploit actually uses an ESP32 development kit to conduct attacks on target devices.
BrakTooth severity and impact varies for every device
The number of affected devices is believed to be in billions. However, the impact is different based on the device’s underlying SoC board and Bluetooth software stack.
The worst vulnerability part of the BrakTooth findings is CVE-2021-28139. This vulnerability allows attackers to run their own malicious code on vulnerable devices via Bluetooth LMP packets - remotely.
According to the research team, CVE-2021-28139 affects smart devices and industrial equipment built on Espressif Systems’ ESP32 SoC boards, but the issue is bound to impact many of the other 1,400 commercial products some of which are bound to have reused the same Bluetooth software stack.
Here’s a YouTube video that explains this in depth: BrakTooth - Arbitrary Code Execution on ESP32 via Bluetooth Classic (BR/EDR)
Other BrakTooth issues are less severe but still annoying. For example, there are several vulnerabilities that can be used to crash the Bluetooth service on smartphones and laptops by flooding devices with malformed Bluetooth LMP (Link Manager Protocol) packets. Microsoft Surface laptops, Dell desktops, and several Qualcomm-based smartphone models are vulnerable to these attacks.
Here’s a YouTube video that explains this: BrakTooth - Invalid Timing Accuracy attack on Qualcomm based phones
In addition, attackers can also use truncated, oversized, or out-of-order Bluetooth LMP packets to crash devices altogether, which will require a manual reboot, as seen in the demo below.
Here’s a YouTube video that explains this: BrakTooth - Feature Response Flooding on Audio Products
The research team said that all the BrakTooth attacks could be carried out with off-the-shelve Bluetooth equipment that costs less than $15.
Here’s the breakdown:
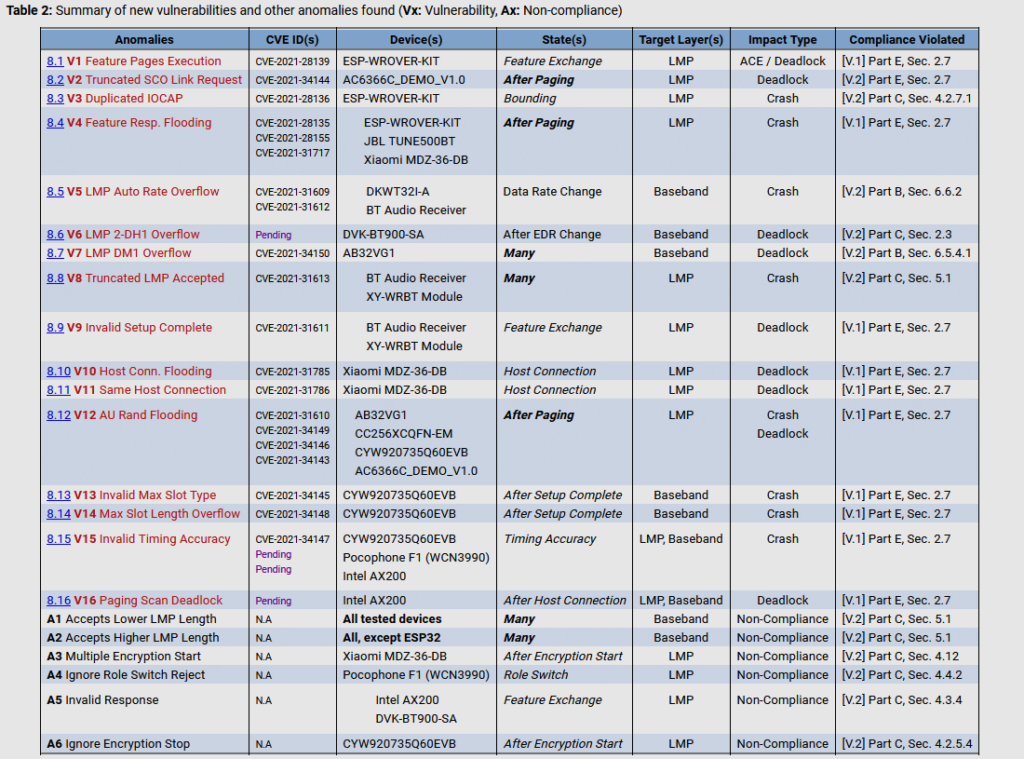
Figure 2: Summary of new vulnerabilities and other anomalies
Are the affected vendors aware of this chaotic BrakTooth?
Yeap! The security researchers have already reached out and informed them
Some companies have already released firmware patches to address the vulnerability, others are investigating the issue, and a few have said they don't plan to fix the flaw.
A spokesperson for the Bluetooth Special Interest Group, which governs the development of the Bluetooth standard, said they’re aware of these issues but couldn’t pressure vendors into patches since these issues don’t impact the standard itself, but each vendor’s own implementation.
The Singapore University of Technology and Design researchers said they don't plan to publicly release the full proof of concept exploit until the end of October 2021 because that's when Intel is supposed to patch its devices. However, they did release instructions for "a low-cost BT Classic (BR/EDR) Active Sniffer" that will use the proof of concept exploit when it's released. They have set up a web form instead where vendors can approach them and request the code to test devices on their own.
In the last 2 years, Bluetooth has met with many challenges in terms of vulnerabilities. These are some security flaws that impact the protocol and its implementations that have been disclosed so far: BLESA, BLURtooth, BIAS, SweynTooth, KNOB.
Details about future patches released after this blog’s publication, along with technical details about the BrakTooth vulnerabilities, are available on this dedicated website.
So, there you have it! For more interesting news and updates, sit tight and stay tuned.
Until next time, friends!
Credits: PCMag Asia, The Record